Blog
The Bedrock of Ethical Hacking II
Emmanuel Umelo
Posted: July 16, 2025

The Bedrock of Ethical Hacking II
In our last content, we explored the non-intrusive and covert nature of passive reconnaissance. We highlighted, for instance, how its undetectability can be a weapon in the hands of malicious actors and extensively cited tools specific to conducting one. However, today’s content will focus on active reconnaissance, where we will attempt to use case scenarios to explain its woven intricacies.
What is Active Reconnaissance
Active Reconnaissance is the direct interaction with the target to gather information. In this type of reconnaissance, the risk is considerably higher. It has the potential to trigger security alerts and defences. Unlike passive recon, it leaves logs, traces, and even footprints on your target's server.
Note : Before you conduct active recon as a cybersecurity professional, ensure you are authorised and have explicit permission to carry out this operation on any organisation.
Why Active Recon Matters
- Detailed Vulnerability Assessment
- Help identify attack vectors
- Comprehensive Understanding of Target Environment
- Enabling proactive security measures
- Information Gathering
- Insight into Target Environment
- Essential for Penetration Testers
Methods and Techniques
- Port Scanning: This involves scanning the target's system for open ports. Tools like Nmap and Nessus are commonly used for this purpose. The goal is to identify open ports and the services running on them.
- Banner Grabbing: This technique is used to gather information about the software running on open ports, including the version and type of software.
- Network Mapping: Active reconnaissance can be used to understand the layout of the network, identifying routers, firewalls, and other network devices.
- Vulnerability Scanning: Tools are used to actively probe systems for known vulnerabilities. This can help in identifying potential entry points for further attacks.
- Web Enumeration: Strategies in gathering useful information like services running, ports, directories, and other useful resources that can be used in exploitation.
Understanding Active Recon: Case Scenario
Scenario Overview:
In demonstrating how active recons are conducted, we will demonstrate using a simulated environment how an external penetration test is conducted. For this case, let's assume an organisation hired a pentester to conduct a vulnerability assessment and pen-test their systems, networks, and public-facing infrastructure. This time, we are targeting the web server.
Lab Simulation: Active Recon on a Target Web Server
- Attacker Machine: Kali Linux or Parrot OS
- Target: Metasploitable 2 (simulated in a lab environment)
- Objective: Gather much intel and information from the target (victim), identify services, open ports, technologies, subdomains, and potential vulnerabilities.
Step-by-Step Walkthrough:
These steps show the purpose behind why specific tools are used to conduct this test.
Step 1: Ping Target.
To test the reachability of a host (like a website or IP address) over an IP network, and measure the round-trip time it takes for packets to travel to and fro between your machine and the target, use the command:
ping -c 10 192.168.40.131
Why use Ping?
- It is the first approach when conducting an active recon.
- It sends ICMP (Internet Control Message Protocol) Echo Request packets to the target, checking the status of the network.
- If reachable, the target system replies with an ICMP Echo Reply.
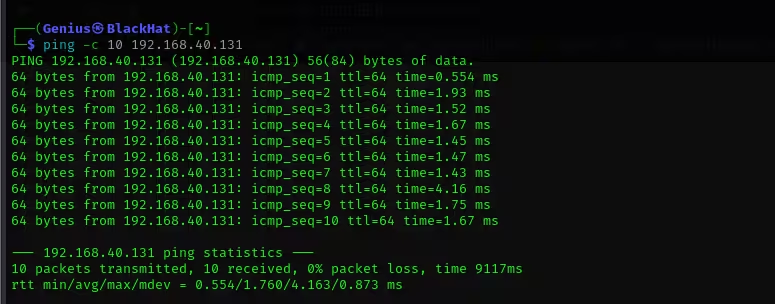
Ping output: ping -c 10 192.168.40.131
- ping: A network utility used to test the reachability of a host and measure the round-trip time (RTT) for messages sent.
- -c 10: Specifies that 10 packets should be sent.
- 192.168.40.131: The domain being pinged (resolved to IP: 192.168.40.131).
- 64 bytes: Size of the ICMP Echo Reply packet received.
- 192.168.40.131):( IP address of the host.
- icmp_seq=1: The sequence number of the ICMP request (1st packet, then 2nd, etc.).
- ttl=64: Time To Live value. Indicates how many hops (routers) the packet can go through before being discarded.
- time=1.52 ms: Round-trip time it took for the packet to go to the server and back.
Step 2: Performing Network Scanning.
To discover hosts and services on the target network, we perform a network scan with the Nmap (Network Mapper) tool.
Result Explanation
Command example: nmap -sT -sV -O 192.168.40.131
- -sT: TCP Connect Scan (uses the full TCP handshake). It's used when SYN scan (-sS) is not possible (e.g., without root privileges)..
- -sV: Version detection- tries to determine the software and version running on each port.
- -O: OS detection - attempts to guess the operating system of the target.
- 192.168.40.131: The IP address of the target machine (likely inside a local virtual lab).
Nmap Summary
The result of the Nmap scan shows ports running and open. It also displays the services and versions available on the target. This way, an attacker could identify possible entry points to exploit.
Step 3: Checking for Hidden Files on the Web server
To check for any hidden files and directories on the web server, the Gobuster tool is used.
Result Explanation
Command example: gobuster dir -u http://192.168.40.131 -w [wordlists].:
What Each Part Means:
- gobuster: The tool being used (version 3.6 in this case).
- dir: Directory/URL brute-forcing mode (as opposed to DNS or S3 modes).
- -u: Target URL. In this case, it's scanning the 192.168.40.131 website.
- -w: Wordlist used for brute-forcing possible directories or files. This is a medium-sized wordlist from the DirBuster collection, commonly found on Kali Linux or Parrot OS.
Use Case / Context
- Typically used to perform web application penetration testing.
- Discover hidden or unlinked content.
- Access admin panels or sensitive endpoints..
- Uncover potential vulnerabilities in less-visible parts of the site..
Step 4: Scan Technologies & Software used by the target
To achieve this, we will use WhatWeb, a web scanner that helps identify the detect the software used by websites. It can detect:
- Web servers (Apache, Nginx, IIS)
- CMS platforms (WordPress, Joomla, Drupal)
- JavaScript libraries (jQuery, Angular, React)
- Frameworks (Laravel, Django, ASP.NET)
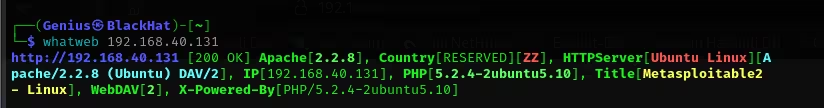
Result Explanation
The output gives the domain name of the target, the IP address, the HTTP header, and the software and technology it is run on.
Step 5: Scan for potential vulnerabilities.
To check for vulnerabilities in the web server, Nikto can be used. While it is an open-source vulnerability scanner, it is used to perform comprehensive tests to find security issues, misconfigurations, and potential vulnerabilities.
Result Explanation
- Target IP: The target IP
- Target Hostname: The hostname of the target)
- Target port: The port on which the target website is running
- SSL info: The valid certificate of the target website, TLS, and the Issuer.
Step 6: Checking for Subdomains
Amass is an open-source reconnaissance tool that can help check for subdomains. Used for both passive or active reconnaissance, it helps pen-testers map out the public attack surface of a target organisation.
To illustrate, we use the command:
amass enum -active -brute -w -d
Result Explanation
- -active: Tells us that it is an active scan/recon
- -brute: Brute-forcing for as many subdomains as possible using the wordlists
- -w: Wordlists (list of DNS & Subdomains) aids for bruteforcing.
- -d: Domain (the name of the target website)
- Amass: Tool name (a CLI-based tool)
- enum: To search and fish out other/hidden subdomains connected to the target
Lab Simulation: Result Evaluation
With the use of the active recon tools, we have been able to successfully interact with our target system. We could extract core pieces of information that help us identify open ports, technologies and software used, and the potential vulnerabilities associated with our target, Metaploitable 2.
Ethical and Legal Considerations
While active reconnaissance can be a powerful tool in the arsenal of an ethical hacker, it comes with significant ethical and legal considerations. It requires:
- Permission and Authorisation before engaging a target system of an organisation.
- Respecting the Privacy of data associated with the target organisation
- Minimising Impact to ensure core operations are not disrupted.
- Compliance with Laws and Regulations to avoid severe legal consequences.
Active Reconnaissance Tools & Function
| Tool Name | Category | Functions | Type | Cost |
|---|---|---|---|---|
| Ping | Network connection | Verifies network connectivity between your machine and the target. | Command-line (CLI) | Free |
| Gobuster | Find hidden files and directories | Directory and file brute-forcing on web servers | Command-line (CLI) | Free |
| Whatweb | Detects web technologies (CMS, frameworks, plugins) | WhatWeb is a web scanner that identifies technologies and software used by websites. | Command-line (CLI) | Free |
| Nikto | Web server vulnerability scanner | Open-source web server scanner for misconfigurations, outdated software, etc. | Command-line (CLI) | Free |
| Enum4linux | SMB enumeration tool | Scans for users, shares, OS, binaries for vulnerabilities leading to privilege escalation. | Command-line (CLI) | Free |
| Nmap | Network mapping | Discovers hosts and services on a network through scanning. | Open Source | Free |
| AMASS (Active mode) | Active Subdomain, DNS enumeration | DNS enumeration and subdomain brute-force (with -active flag). | Command-line (CLI) | Free |
| Metasploit Framework | Active exploitation, service enumeration, vulnerability scanning | Collection of exploits, payloads, post-exploitation tools, simulating real-world attacks. | Open Source | Free |
References:
Ethical Hacking- Reinvent Security | Cybersecurity Laws and Regulations - Canada (ICLG)